Cybersecurity, CMMC, and SAM: The Trio Every DoD Contractor Needs to Master
As cybersecurity threats grow more sophisticated, the U.S. Department of Defense (DoD) is raising the bar for its contractors. Achieving and maintaining CMMC (Cybersecurity Maturity Model Certification) compliance is no longer optional—it’s a contract requirement. Yet, many contractors overlook one of the most foundational elements of cyber readiness: Software Asset Management (SAM).
In today’s high-risk environment, organizations need a complete and accurate inventory of their IT ecosystem to stay compliant, secure, and audit-ready. That’s why The SIE Group—with its deep expertise in federal software management—frequently works alongside trusted cybersecurity providers like Belarc to support clients pursuing CMMC compliance with automation and visibility.
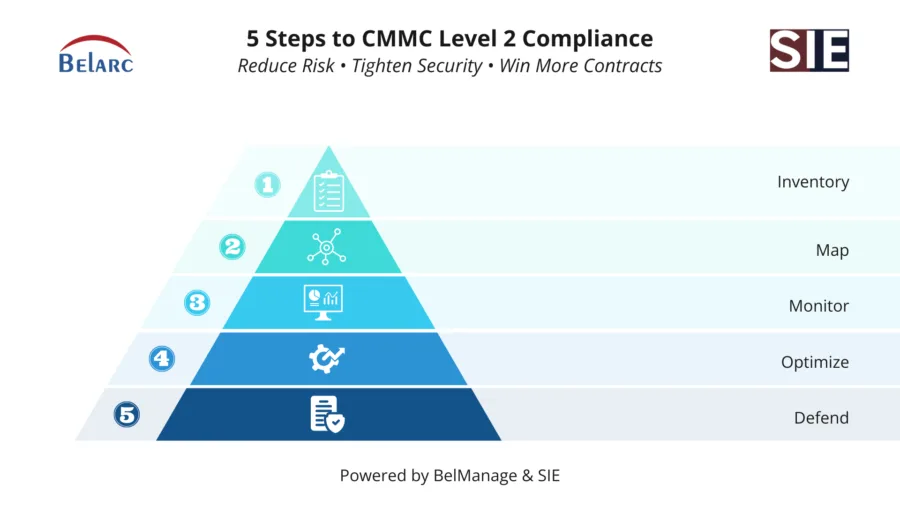
Why CMMC Compliance Starts With Visibility
Whether you're pursuing CMMC Level 1 (Foundational) or Level 2 (Advanced), one constant remains: you can’t protect what you don’t know you have.
CMMC 2.0
places a strong emphasis on controls like:
- Asset Management (AM):
Maintain accurate inventories of hardware and software.
- Configuration Management (CM): Establish and enforce secure configurations.
- Risk Management (RM):
Identify and mitigate risks associated with software vulnerabilities.
Unfortunately, many DoD contractors still struggle with outdated spreadsheets, incomplete asset inventories, or unmanaged software across their environments. This isn’t just an operational issue—it’s a compliance risk.
Software Asset Management: The Cybersecurity Backbone
Software Asset Management is often perceived as a cost optimization strategy—and while SAM does help reduce unnecessary software spend, its real value in the DoD contracting space lies in its ability to fortify cybersecurity and support CMMC requirements.
With a SAM-driven approach, organizations can:
- Identify unauthorized or vulnerable software before it becomes an attack vector.
- Enforce secure configurations and licensing policies that align with CMMC control objectives.
- Enable rapid response to vendor audits, security breaches, and compliance assessments.
The bottom line? SAM is a compliance multiplier. It enhances cybersecurity while ensuring your organization is always audit-ready.
Combining Advisory Expertise with Proven Tools
At SIE, we’ve helped federal agencies manage over $500M in software annually—delivering cost savings, audit defense, and IT asset control. When clients require enhanced automation and real-time visibility into their software environments, we often recommend tools like those provided by Belarc, a leader in IT security assessment and compliance automation.
What Belarc’s Technology Offers
- BelManage: Builds a real-time, centralized inventory of software, hardware, and configurations across your IT estate.
- BelSecure: Automatically scans and benchmarks systems against CMMC, NIST 800-171, FISMA, DISA STIGs, and more, delivering actionable dashboards and compliance reports.
Together, these capabilities provide DoD contractors with the clarity and control needed to meet today’s compliance standards and defend against tomorrow’s threats.
What’s at Stake for DoD Contractors
Failing to meet CMMC requirements can result in:
- Lost contract opportunities
- Increased risk of cyber incidents
- Costly remediation and legal exposure
- Failed audits and reputational damage
By aligning cybersecurity, SAM, and CMMC, you’re not just avoiding risk—you’re building a stronger, more competitive business.
Get a CMMC Readiness Check—At No Cost
The path to CMMC compliance is complex—but you don’t have to walk it alone. The SIE Group
can guide you through the strategy, while tools like Belarc help bring your systems into focus.
About the Authors
The SIE Group is a Service-Disabled Veteran-Owned Small Business (SDVOSB) helping federal agencies and contractors optimize software assets, reduce costs, and improve compliance across IT investments.